It’s critical to keep one step ahead of attackers in the constantly changing field of cybersecurity. Organisations are looking to novel solutions to strengthen their defences in response to the growing sophistication of cyber threats. Platforms for bug bountys are one such alternative that is gaining popularity. By crowdsourcing security testing, these platforms offer a proactive approach to cybersecurity and enable organisations to take advantage of the global community of ethical hackers’ aggregate experience. We’ll go into the world of bug bounty platforms in this post, discussing their advantages, how they operate, and how businesses may take full advantage of them to improve cybersecurity.
Benefits of Bug Bounty Platforms:
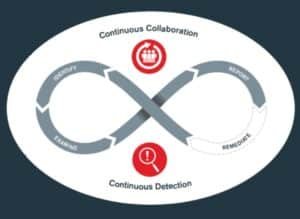
Continuous security testing: In addition to more conventional security methods like vulnerability assessments and penetration testing, bug bounty sites allow organizations to perform constant testing for security. This continuous testing lowers the attack surface of the organization by ensuring that recently found vulnerabilities are swiftly fixed.
 |
Access to Global Talent: Organizations can obtain a variety of viewpoints and skill sets by reaching out to a worldwide community of ethical hackers. The possibility of finding intricate and hidden vulnerabilities that internal security teams might have missed is increased by this varied talent pool. |
Cost-Effective Security: Compared to conventional security testing techniques, bug bounty programs are more affordable since they use a pay-for-results basis. Organizations only pay for vulnerabilities that have been validated, as opposed to paying set costs for recurring assessments. This encourages ethical hackers to find and submit as many problems as they can.
Improved Reputation: By putting in place a bug bounty programme, an organisation can show its dedication to accountability and the field of cybersecurity, which will benefit its standing with partners, clients, and the cybersecurity community. Positive relationships and ongoing involvement can also be fostered by publicly recognising and praising ethical hackers for their accomplishments.
Selecting the Best Platform for Bug Bounties:
Choosing the appropriate bug bounty platform is essential to the program’s success. When assessing possible platforms, take into account the following factors:
Reputation and Track Record: Select a platform that has a history of effectively enabling bug bounty programs for businesses in a comparable size and sector. Seek out platforms that place a high priority on ethics, security, and openness.
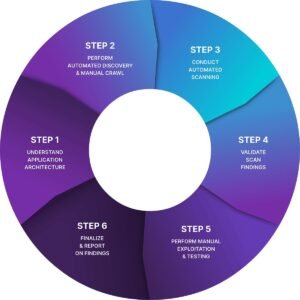
Scope and coverage: Examine the system’s scope and breadth with respect to various asset kinds, such as web apps, mobile apps, IoT devices, and infrastructure elements. Make sure that the system is compatible with the platforms and innovations which the organization uses.
 |
Community Quality: Evaluate the calibre and level of experience of the ethical hacking community on the site. Seek for platforms that thoroughly screen and educate its hackers in order to guarantee high-caliber submissions and reduce false positives.
Reporting and Communication: Take into account the platform’s reporting and communication features, such as how simple it is to report vulnerabilities, follow the progress of submissions, and get in touch with the platform’s administrators and ethical hackers.
Support and Escalation: Make sure that in the event of a significant or urgent vulnerability, the platform offers sufficient support and escalation procedures. Seek for platforms that enable quick coordination between organizational stakeholders and ethical hackers and provide assistance around the clock.
Increasing Cybersecurity Victories:
In order to optimize cybersecurity gains via bug bounty programs, entities ought to embrace a proactive and cooperative strategy:
 |
Establish Specific Goals: Clearly state the objectives and parameters of the bug bounty programs, including the categories of vulnerabilities covered, the payment schedule, and the anticipated results. Openly share these goals with the bug bounty community as well as those within the organization.
Interact with Ethical Hackers: Encourage cooperative and courteous relationships with ethical hackers that take part in the bug bounty scheme. Give hackers access to materials and clear instructions so they can comprehend the organization’s security procedures, reporting procedures, and technology stack.
 |
Set Remediation as a Top Priority: Aggressively classify and rank vulnerability reports according to their seriousness and possible influence on the resources and activities of the company. Ensure that resources are allocated to promptly address both critical vulnerabilities and issues of lesser severity.
Continuous Enhancement: Ethical hackers, organizational stakeholders, and platform administrators provide input on how to improve the bug bounty programme on an ongoing basis. Find areas where the program can be made more successful and efficient by using technology, communication, and process improvements.
Bear in mind:
| Be Up to Date: The world of cybersecurity is always changing. Make time to be informed about new risks, weaknesses, and preventative measures.
Make an Open Source Contribution: You may improve your reputation and draw in opportunities by giving back to the community with your skills and expertise. |
 |
To sum up:
By leveraging the combined knowledge of ethical hackers worldwide, bug bounty systems provide businesses with a proactive and economical approach to cybersecurity. Businesses may test and improve their safety measures on a constant basis, counter new threats, and gain the trust of partners and consumers by interacting with bug bounty programs. Organizations may optimize cybersecurity gains and maintain a lead over changing cyber threats by carefully choosing the appropriate platform and embracing a collaborative mentality.