It is critical to protect your network in the constantly changing digital world. A familiar sentinel watching over the network boundary awaits you: the firewall. Let’s examine the principles, varieties, and methods by which firewalls protect your online environment.
What Is a Firewall?
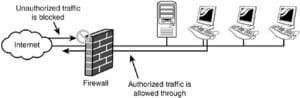
As a gatekeeper, a firewall filters network traffic in accordance with pre-established security policies. Think of it like a watchful doorman at a private club; it lets in only the smartly dressed patrons and keeps miscreants out.
How Does It Work?
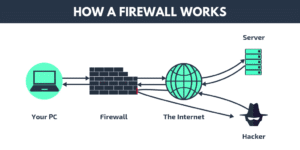
A firewall monitors all incoming and outgoing network traffic, serving as a kind of security guard. It safeguards your devices and data by letting safe data through while preventing erroneous or suspicious traffic.
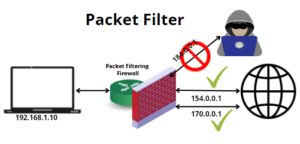
1. Packet Filtering: Stateless or Packet Filtering Firewall
As data packets move over the network, this firewall inspects each one individually. To determine whether they are welcome or not, it looks at their source, destination, and other characteristics. Consider it similar to sorting mail: keeping the important correspondence and throwing out the unnecessary ones.
2. Stateful Inspection Firewall
- This firewall keeps track of a state table, in contrast to the prior model. It retains the background of continuing relationships.
- It verifies a packet’s authenticity by comparing it to the status table as it arrives.
- Consider it as a watchful librarian who is aware of the books that have already been checked out.
3. Circuit-Level Gateway
- This firewall verifies connections while operating at Layer 4, or the transport layer.
- It verifies that the connection configuration complies with the guidelines but does not examine the contents of the packets.
- Think of it as an officer checking passports to make sure people are allowed to enter.
4. Application-Level Gateway (Proxy Firewall)
- This firewall type, which is the most advanced, examines data at the application layer.
- It serves as a go-between for internal users and outside services.
- Imagine it acting as a language interpreter, translating requests from one person to another.
5. Next-Generation Firewall (NGFW)
- The firewall equivalent of Superman, NGFW combines conventional filtering with revolutionary features.
- It examines user identification, content, and application behavior in addition to packets.
- See it like an infinite investigator, able to identify even the most subtle dangers.
Evolution of Firewalls
1. Generation 1: Antivirus Protection
- In the 1980s, firewalls focused on antivirus defenses against PC-invading viruses.
2. Generation 2: Network Protection
- Mid-1990s saw the rise of physical firewalls safeguarding entire networks.
3. Generation 3: Application Security
- Early 2000s brought firewalls addressing application vulnerabilities.
4. Generation 4: Payload Defense
- Around 2010, firewalls tackled evasive and polymorphic attacks.
5. Generation 5: Large-Scale Protection
- By 2017, advanced threat detection became crucial due to complex attack methods.
Software vs. Hardware Firewalls
1. Software Firewalls (Host Firewalls)
- Safeguard specific gadgets, or hosts, such PCs and smartphones.
- Operating systems bundle them together, and they examine local traffic.
- Similar to a private bodyguard for your gadget.
2. Hardware Firewalls (Network Firewalls)
- Preserve complete networks.
- Utilise hardware appliances that are committed.
- See your network as being surrounded by a strong wall.
3. Cloud-Based Firewalls:
- With centralised management and scalability, these firewalls are hosted in the cloud.
- Convenient as they are, they nevertheless require a steady internet connection and could cause latency.
Importance of Firewalls:
Network Segmentation:
By splitting a network into several smaller subnetworks, each with its own set of security policies, firewalls allow for network segmentation. This lessens the amount of harmful activity that spreads throughout the network and helps to contain breaches.
Access Control:
Firewalls stop illegal access to sensitive resources and applications by implementing access control restrictions. In order to lessen the attack surface and minimize potential security concerns, they can restrict access based on user identities, originating IP addresses, or the type of traffic.
Threat Prevention:
With their ability to filter out dangerous information, block known malicious IP addresses, and identify and stop abnormal network traffic patterns, firewalls are essential tools for preventing threats. In addition to ransomware, malware, and denial-of-service (DoS) violence, they offer proactive defence against a variety of cyber threats.
Choosing the Right Firewall :
Based on your unique requirements and available resources, the best firewall solution will vary. Take into account elements like:
- Network size and complexity: A hardware firewall may be necessary for larger networks with more devices in order to provide strong security.
- Technical expertise: Perhaps a managed firewall service would be a better choice if you are not very tech-savvy.
- Budget: Software firewalls are frequently free but may provide less protection than hardware firewalls, which might be costly.
Best Practices for Firewall Configuration
1. Block Traffic by Default
- Implement a rigorous policy at first, allowing only those things that are specifically allowed.
- Reject any unknown or suspicious traffic.
2. Specify Source and Destination
- Establish rules based on port numbers and IP addresses.
- Be clear about who has access to what information.
3. Regularly Update Your Firewall Rules
- Stay informed about new dangers.
- Modify your guidelines in light of evolving events.
Best Practices for Firewall Implementation:
1. Define Clear Security Policies:
Clearly define the kinds of traffic that are allowed or prohibited depending on organisational needs and risk tolerance in comprehensive security policies. To keep up with changing business requirements and security concerns, evaluate and update these policies on a regular basis.
2. Layered Defense:
Combine several security technologies, such as firewalls, intrusion detection systems (IDS), and antivirus software, to implement a layered approach to security. Because of the defence in depth offered by this multifaceted strategy, it is more difficult for attackers to compromise the network.
3. Regular Audits and Monitoring:
Make that firewall configurations and rule sets are in line with compliance standards and security best practices by conducting routine audits of them. To further avoid potential security incidents, keep an eye out for any suspicious behaviour in firewall logs and alerts and look into abnormalities right once.
4. Keep Software Up-to-Date:
Update the firmware and software of your firewall on a regular basis to fix known vulnerabilities and guarantee top performance. To reduce risks in advance, keep up with new threats and security updates from firewall manufacturers.
Points To Be Remembered:
Keep in mind that your first line of defence is a properly set firewall. It’s important to let the correct people join your virtual celebration while keeping the disruptive people out, not only to block them. Now let the firewall take monitor and erect your virtual drawbridge!
Conclusion
Organizations can improve their security posture and diminish the risk of data breaches and cyberattacks by having a solid understanding of firewall principles and putting best practices for their deployment into practice. A strong firewall is still necessary to protect important assets and ensure network integrity, even as the cybersecurity landscape changes.