Introduction
Malware, which is short for malicious software, is a serious global threat to people and organisations. Reverse engineering is a technique used by cybersecurity experts to analyse and comprehend the operation of malware in order to effectively counter these threats. This article will examine the steps involved in reverse engineering malware, its significance for cybersecurity, and the instruments and methods employed in this domain.
Understanding Malware
Any software intended to interfere with, harm, or obtain unauthorised access to a computer system is known as malware. Malware frequently takes the form of ransomware, worms, Trojan horses, and viruses. These malicious programmes have the ability to steal confidential data, interfere with operations, and result in losses of money.
Importance of Reverse Engineering Malware
Reverse engineering malware is crucial for several reasons:
1. Understanding the Threat: Cybersecurity experts can learn more about malware’s functionality, capabilities, and intended targets by reverse engineering it. Having this knowledge is essential for creating strong defences against assaults in the future.
2. Developing Countermeasures: Malware analysis can assist in locating software and system vulnerabilities so that these can be patched and future attacks of the same kind can be avoided.
3. Legal and Law Enforcement Purposes: Through the use of reverse engineering, law enforcement organisations can uncover evidence of cybercrimes, bring offenders to justice, and break up criminal networks.
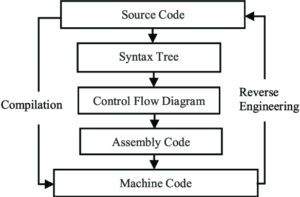
Process of Reverse Engineering Malware
Reverse engineering malware typically involves the following steps:
1. Acquisition: Acquire a malware sample from a malware repository or a live system.
2. Disassembly: To make the logic of the malware’s machine code easier to understand, use a disassembler to convert it to assembly language.
3. Analysis: Examine the deconstructed code to determine the functionality of the malware, including its communication, methods of propagation, and malicious action execution.
4. Reconstruction: To comprehend the general architecture and functionality of the malware, disassemble its high-level code.
5. Documentation: Record the results, mentioning the behaviour, capabilities, and any indicators of compromise (IOCs) of the malware.
Tools and Techniques for Reverse Engineering Malware
Several tools and techniques are used in the reverse engineering process, including:
1. Disassemblers: Assembly language is created from machine code using tools like Ghidra and IDA Pro.
2. Debuggers: Debugging tools like OllyDbg and WinDbg are employed to examine the behaviour of malware while it is being executed.
3. Decompilers: Code analysis is aided by decompilers such as Hex-Rays Decompiler, which can translate assembly code back into a higher-level programming language.
4. Virtualisation: Malware samples can be run in a controlled environment on virtual machines, keeping the host system safe from infection.
Conclusion:
For cybersecurity experts, reverse engineering malware is an essential ability since it enables them to examine and comprehend the inner workings of malicious software. Cybersecurity professionals can create efficient countermeasures and defend against the ever-changing threat of malware by using the appropriate tools and techniques.