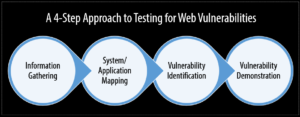
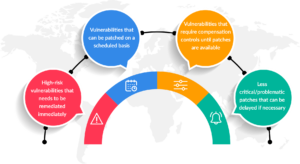
As web apps are essential to our digital infrastructure in a time when cyber dangers are everywhere, it is critical that they be secured. When it comes to keeping up with the constantly changing threat landscape, traditional approaches to vulnerability
identification and classification frequently fall short. There is a current paradigm change in web application security methods, nevertheless, due to the introduction of artificial intelligence (AI). Organisations may augment their defences against malicious attacks by detecting and classifying vulnerabilities more accurately and efficiently by utilising AI-powered technologies.
The Current Landscape of Web Application Security
Everything from e-commerce websites to online banking platforms is powered by web applications, which are widely used. They do, however, also constitute a significant threat to hackers looking to use vulnerabilities for illegal gain. There are limits to how effectively emerging threats can be identified and categorised using traditional vulnerability detection techniques like automated scanning tools and manual code reviews. These methods are inadequate due to human error, time limits, and the sheer complexity of current web applications.
The Role of AI in Enhancing Security
AI has great potential to transform online application security, especially in the area of machine learning techniques. Artificial intelligence (AI)-powered systems are able to identify abnormalities and vulnerabilities with previously unheard-of accuracy and efficiency by utilising massive volumes of data and learning patterns of both benign and malevolent behaviour. Furthermore, AI is capable of evolving and adapting to new threats, hence enhancing its capabilities over time.
Automating Vulnerability Detection
Automating vulnerability detection with AI is one of the main advantages. Manual involvement is a major component of traditional approaches, which can be error-prone and time-consuming. On the other hand, AI algorithms have the ability to automatically examine code, network traffic, and system behaviour in order to quickly spot such vulnerabilities. In addition to speeding up the detection process, this automation relieves cybersecurity experts of some of their workload so they can concentrate on more important duties.
Improving Accuracy through Machine Learning
Due to their superior ability to identify patterns and correlations in data, machine learning algorithms are able to identify tiny indicators of vulnerabilities that may avoid traditional detection techniques. Organisations can improve the quality of their detection systems by using large datasets of known vulnerabilities and attack patterns to train AI models. AI is a powerfully in the continuous fight against cyber attacks since it can also learn from previous events and modify its detection capabilities to new and evolving dangers.
Enhancing Classification of Vulnerabilities
Systems with AI capabilities can be extremely helpful in categorising vulnerabilities according to their seriousness, impact, and exploitability in addition to helping with detection. AI can rank vulnerabilities based on their likelihood of causing harm and direct mitigation measures in that order through extensive analysis of contextual data and risk variables. Through the prioritisation of fixing the most essential vulnerabilities and the reduction of their exposure to cyber hazards, this capacity helps organisations spend their resources more efficiently.
Real-World Applications and Success Stories
AI-powered vulnerability detection and classification has already been adopted by several organisations, with impressive outcomes. To protect sensitive consumer data and stop financial losses, organisations in the financial sector, for instance, have used machine learning algorithms to identify fraudulent activity and unauthorised access attempts in real time. Likewise, IT companies have implemented AI-driven systems to preemptively find and fix flaws in their software before bad actors can take advantage of them.
Overcoming Challenges and Ethical Considerations
Although AI has a great deal of promise to enhance online application security, there are drawbacks and ethical issues associated with it as well. User data privacy and confidentiality must be guaranteed because AI systems may accidentally gather or reveal private information when conducting detection tasks. Furthermore, there’s a chance that biassed AI algorithms will result in vulnerability detection that finds false positives or negatives. Strong data privacy safeguards, open algorithms, and continual monitoring and assessment are all necessary components of a complete strategy to address these issues.
The Future of Web Application Security
Advanced security measures are becoming more and more necessary as cyber attacks continue to grow in sophistication and scope. Web apps can now be significantly better protected against new threats thanks to AI-powered vulnerability identification and classification. Organisations may increase their safety on the internet and reduce the likelihood of cyberattacks by integrating artificial intelligence (AI) to automate detection, improve accuracy, and better classification. To achieve this objective, though, calls for a coordinated effort by cybersecurity experts, tech companies, and legislators to work together, come up with new ideas, and adjust to the dynamic threat environment.
Conclusion:
In summary, by automating vulnerability discovery and classification, AI has the potential to completely transform online application security. Organisations may greatly improve their ability to defend against cyberattacks by using machine learning algorithms to analyse massive amounts of data and spot new risks. But to fully reap the rewards of AI-powered security, issues like algorithmic bias and data privacy must be resolved. Indeed, AI has the potential to be a potent ally in the ongoing fight for cybersecurity with careful preparation, teamwork, and creativity.