A major difficulty in the constantly changing field of cybersecurity is the Advanced Persistent Threat (APT) landscape. Adversaries that carefully plan and carry out lengthy operations to penetrate, steal, and exploit sensitive data from organisations are the targets of these advanced, targeted attacks. APTs are distinguished from regular cyberattacks by their targeted, persistent, and stealthy nature. This necessitates a thorough approach to employee knowledge, organisational policies, and advanced security solutions in addition to detection and mitigation.
Recognising APTs: Features and Strategies
APTs differ from other cyberattacks in several key aspects:
- Targeted: APTs are created with the express purpose of undermining a certain group or person, frequently for motives other than pure profit. Their motivations could stem from sabotage, intellectual property theft, or espionage.
- Stealthy: In order to get beyond traditional security measures, APTs use sophisticated tactics. As they gather intelligence and compromise computers, they take advantage of security holes, install malware, and linger in the target network unnoticed for long periods of time.
- Persistent: As opposed to “smash-and-grab” operations, APTs have longer-term objectives. They take root in the network and modify their strategies on a regular basis to keep access and accomplish their goals.
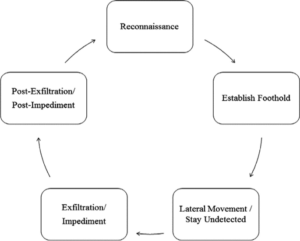
The APT lifecycle typically involves several stages:
- Reconnaissance: Network scanning, social engineering, and open-source intelligence (OSINT) are some of the ways the attacker uses to obtain information about the target organisation.
- Initial compromise: The attacker uses zero-day exploits, watering holes, or phishing assaults to take advantage of weaknesses in the target’s systems.
- Gaining a foothold: By introducing malware or obtaining unauthorised access to user accounts, the attacker makes a name for themselves on the network.
- Lateral movement: In order to increase their reach and obtain sensitive data, the attacker advances laterally within the network, breaking into more accounts and systems.
- Maintaining access: By taking measures to remain persistent within the network, the attacker makes it harder to find and eliminate them.
- Data exfiltration: The hacker uses hidden channels to remove stolen data from the network.
Detecting APTs: Vigilance and Advanced Techniques
APTs are covert, which makes it difficult to find them. On the other hand, a proactive defence can be greatly enhanced by the following techniques:
- Network monitoring: keeping a close eye on network activities to spot any suspicious activity, like strange traffic patterns or unauthorised access attempts.
- Endpoint security solutions: putting in place endpoint protection platforms (EPP) and endpoint detection and response (EDR) systems to identify and stop malware infections and questionable activities on specific devices.
- User behavior analytics (UBA): detecting irregularities in user behaviour that could point to malicious activities or compromised accounts by using UBA tools.
- Security information and event management (SIEM): By combining and analysing security data logs from several sources using a SIEM solution, thorough threat detection and investigation are made possible.
- Threat intelligence: using threat intelligence streams to stay up to date on the most recent APT tactics, methods, and procedures (TTPs) and sharing information with security groups.
Mitigating APTs: A Multi-Layered Approach
Although total protection against APTs cannot be guaranteed by a single solution, the likelihood of successful attacks can be greatly decreased with a multi-layered approach. The following are some crucial tactics:
Establishing effective security policies: Strong security rules that cover data handling procedures, incident response methods, password management, and access control should be put into place and enforced.
Promptly patching vulnerabilities: patching systems and apps for known vulnerabilities on a regular basis to reduce attack surfaces and stop exploitation.
User awareness training: teaching staff members the best ways to maintain cybersecurity hygiene and about phishing and social engineering techniques.
Least privilege principle: giving users only the minimal amount of access necessary for their tasks in accordance with the least privilege concept.
Data encryption: Sensitive data should be encrypted both in transit and at rest to provide an extra degree of security in the event of a compromise.
Incident response planning: creating a thorough incident response strategy that describes what to do in the event of an APT attack that is suspected, including containment, eradication, and recovery techniques.
Security testing and penetration testing: carrying out penetration tests and security assessments on a regular basis to find holes and gaps in the security posture.
Conclusion
The challenge posed by Advanced Persistent Threats to organisations is intricate and dynamic. Organisations may greatly increase their resistance to these sophisticated attacks by comprehending their traits, putting proactive detection mechanisms in place, and implementing a multi-layered mitigation approach. To protect sensitive data and keep a secure digital environment, constant attention to detail, employee education, and continued investment in cybersecurity solutions are essential.